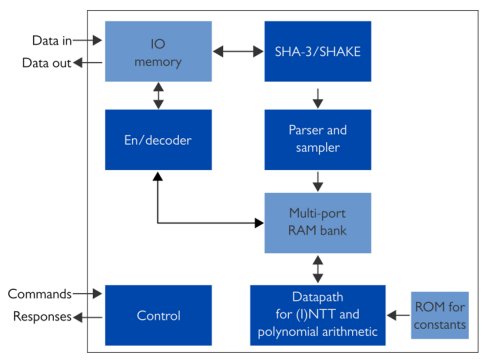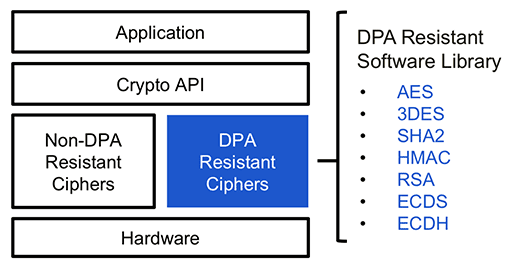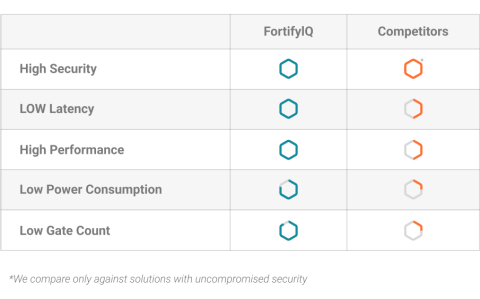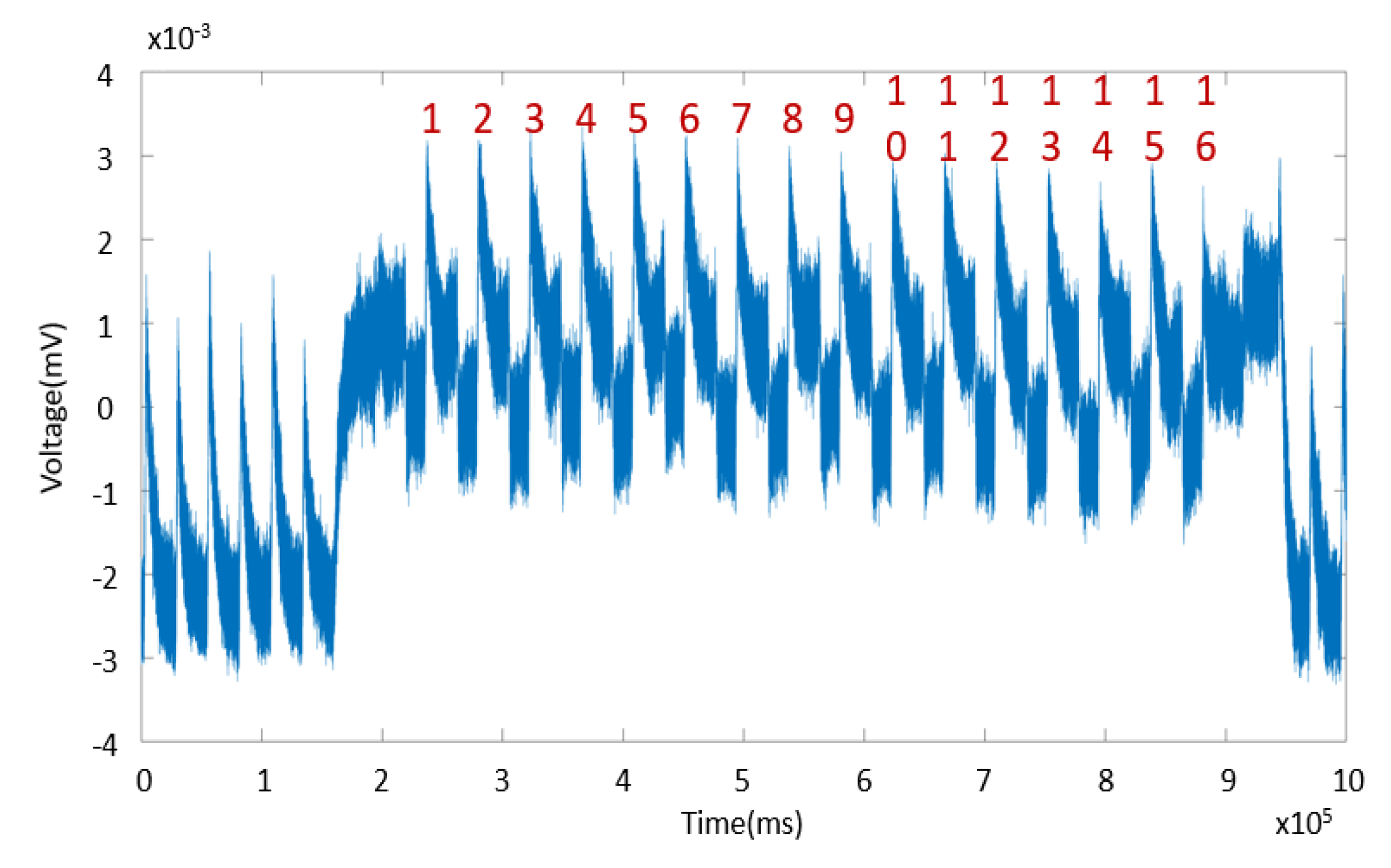
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman

Obscure & Undetected: Hacking Into Hardware of Mission-Critical Infrastructure Using Side-Channel Attacks | 2019-11-14 | Security Magazine
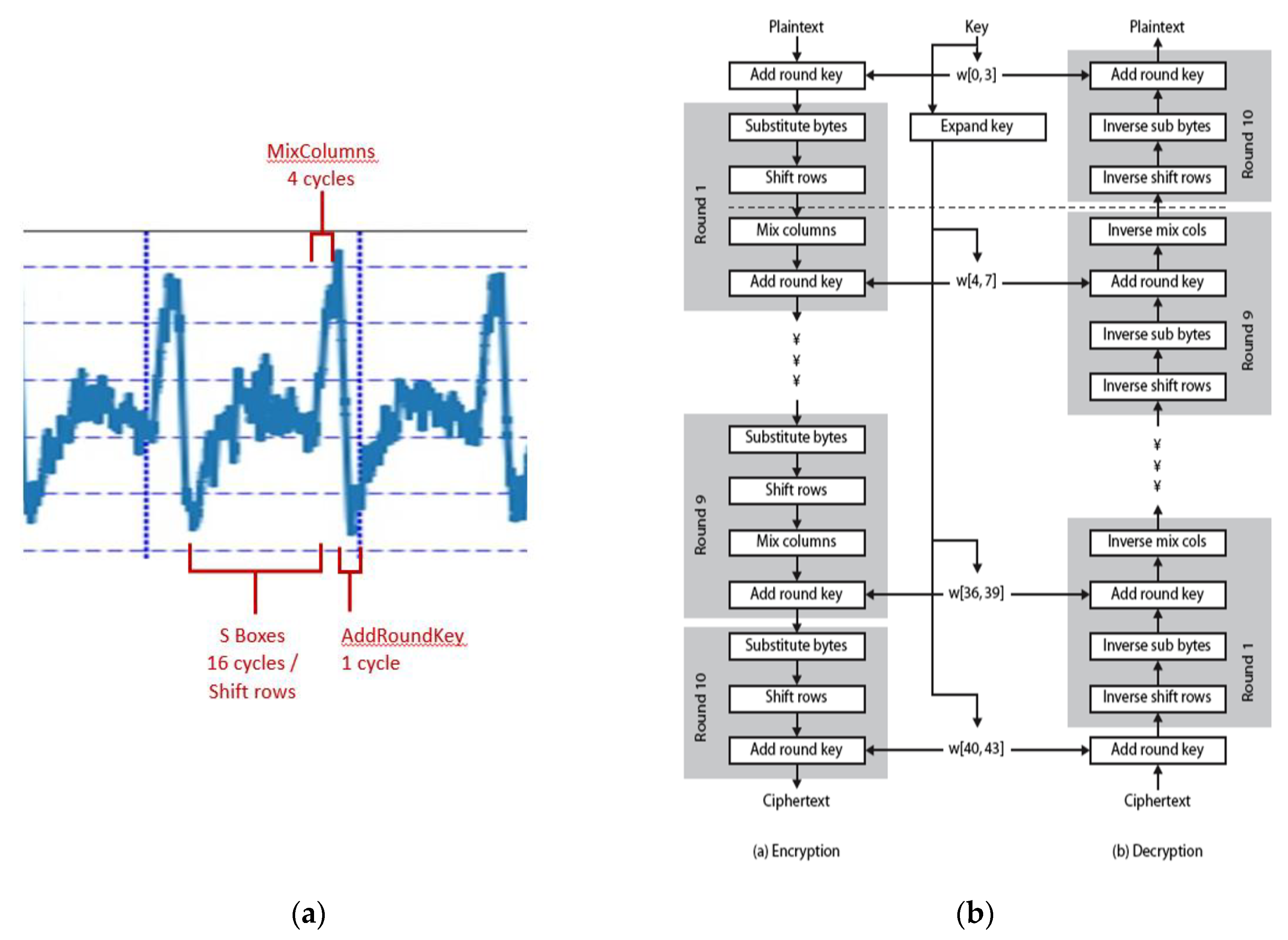
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman
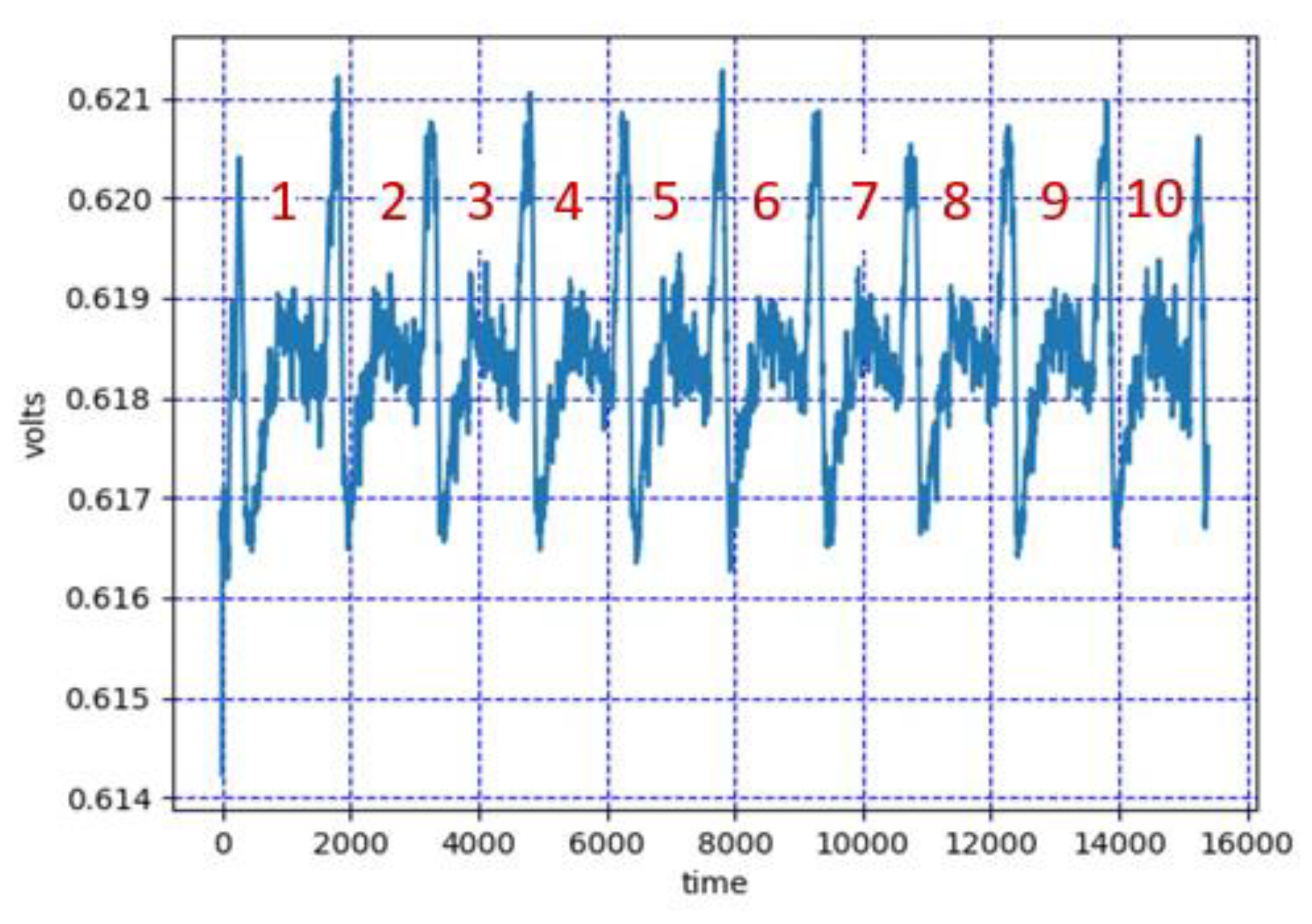
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman
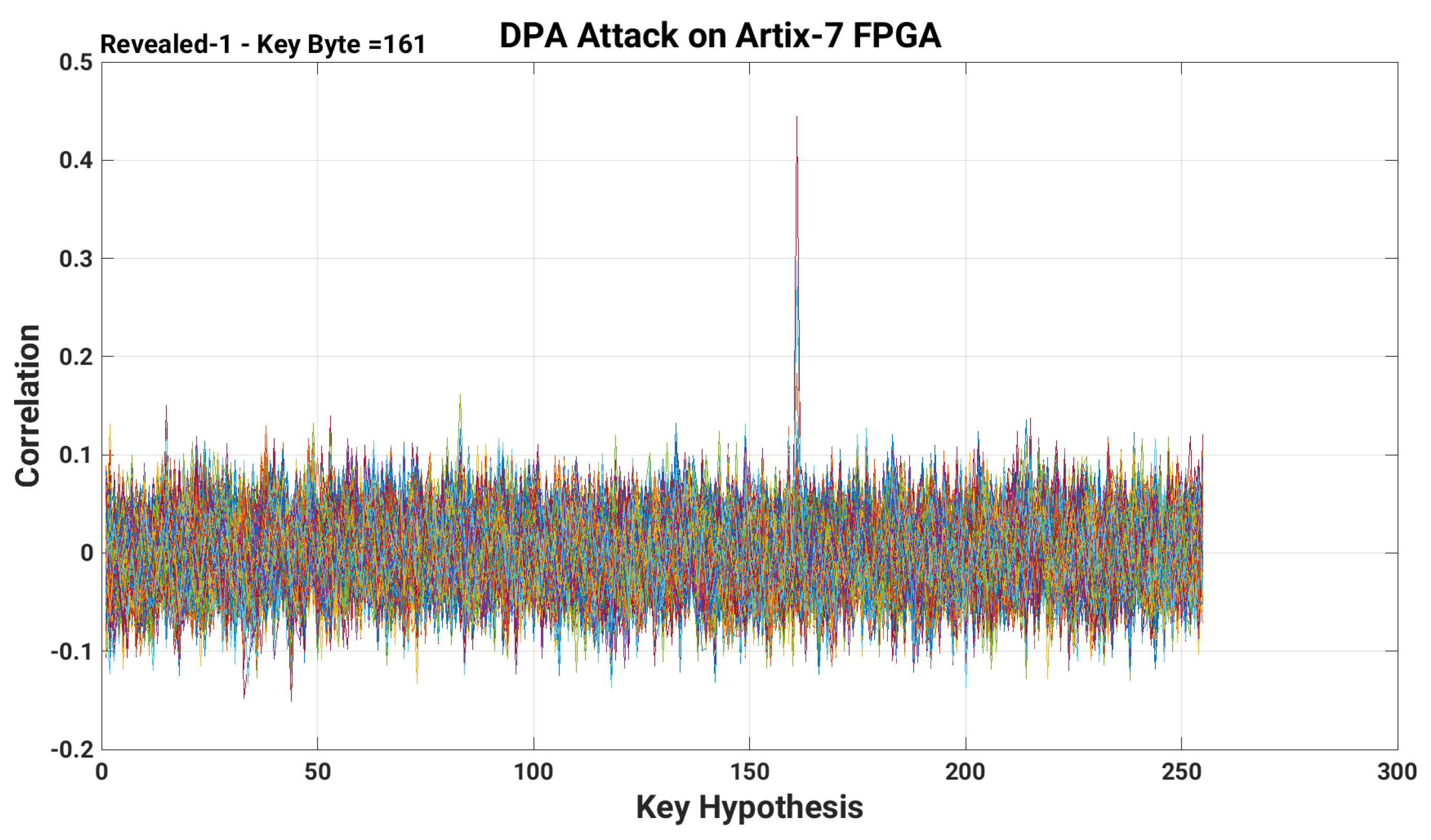
Applied Sciences | Free Full-Text | A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher
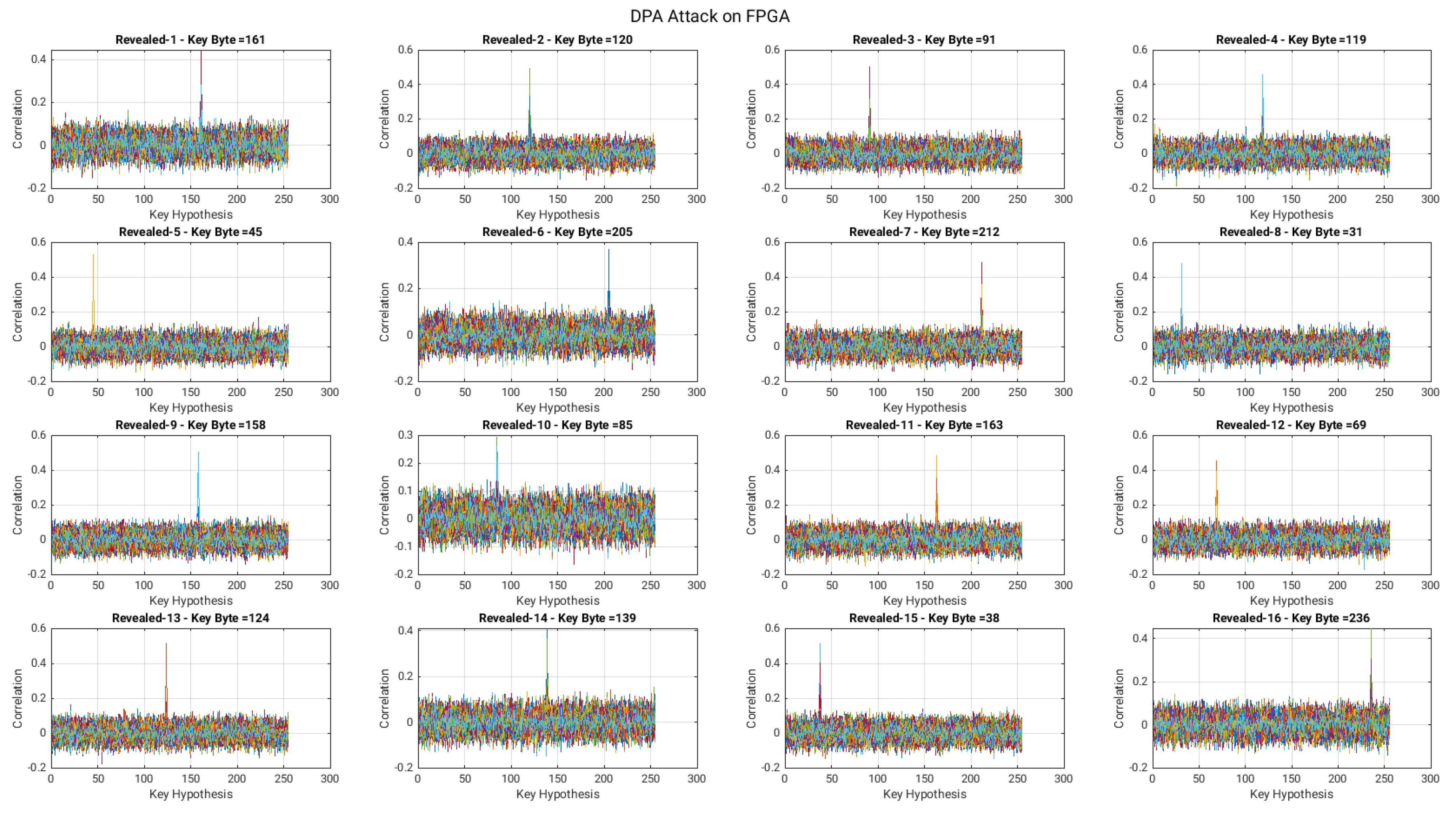
Applied Sciences | Free Full-Text | A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher

Figure 1 from Side-channel attack resistant AES cryptographic circuits with ROM reducing address-dependent EM leaks | Semantic Scholar

Horizontal DPA attack using the traces of the different kP designs and... | Download Scientific Diagram

Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman

PDF) Asynchronous Advanced Encryption Standard Hardware with Random Noise Injection for Improved Side-Channel Attack Resistance
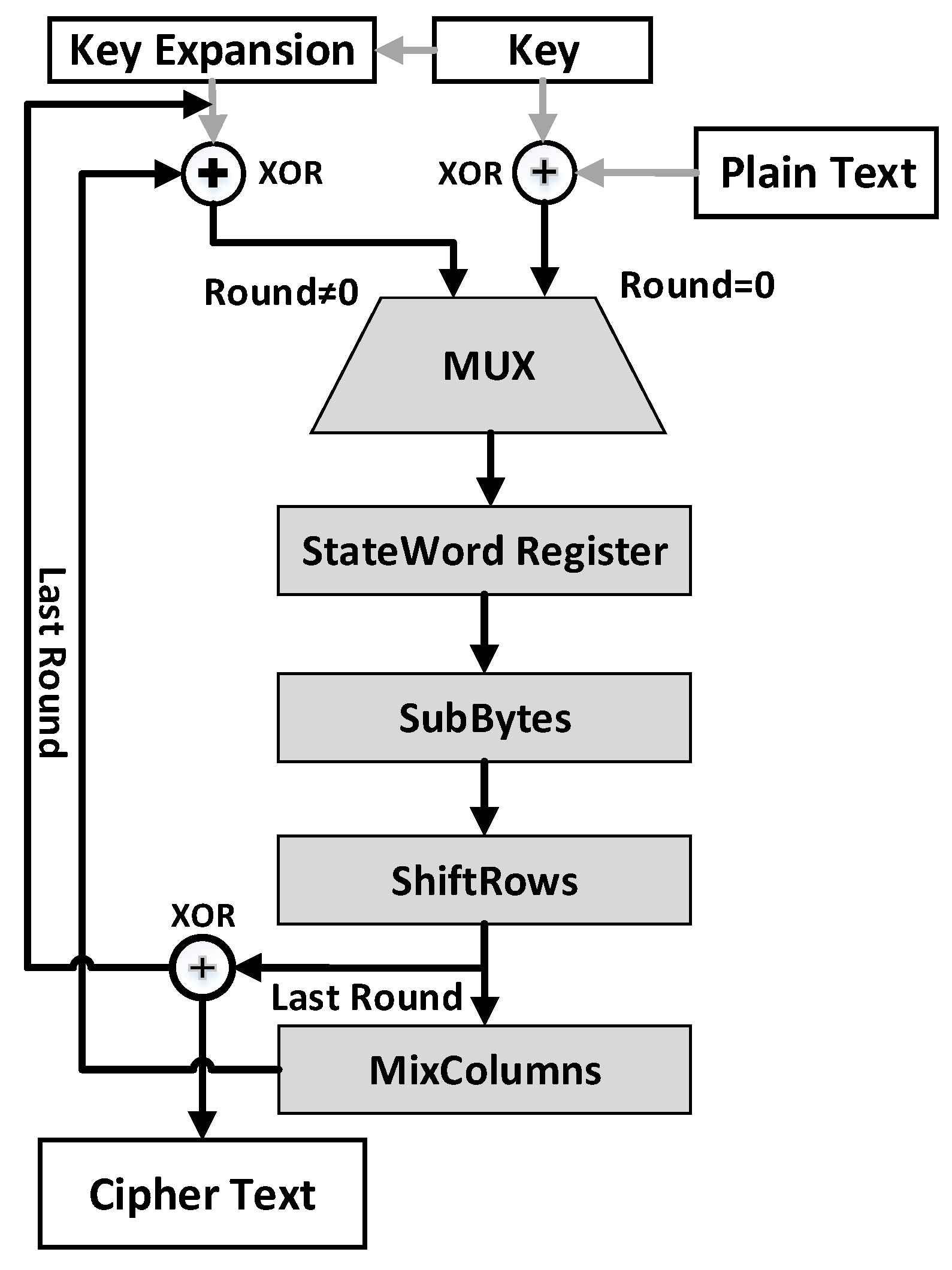
Applied Sciences | Free Full-Text | A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher
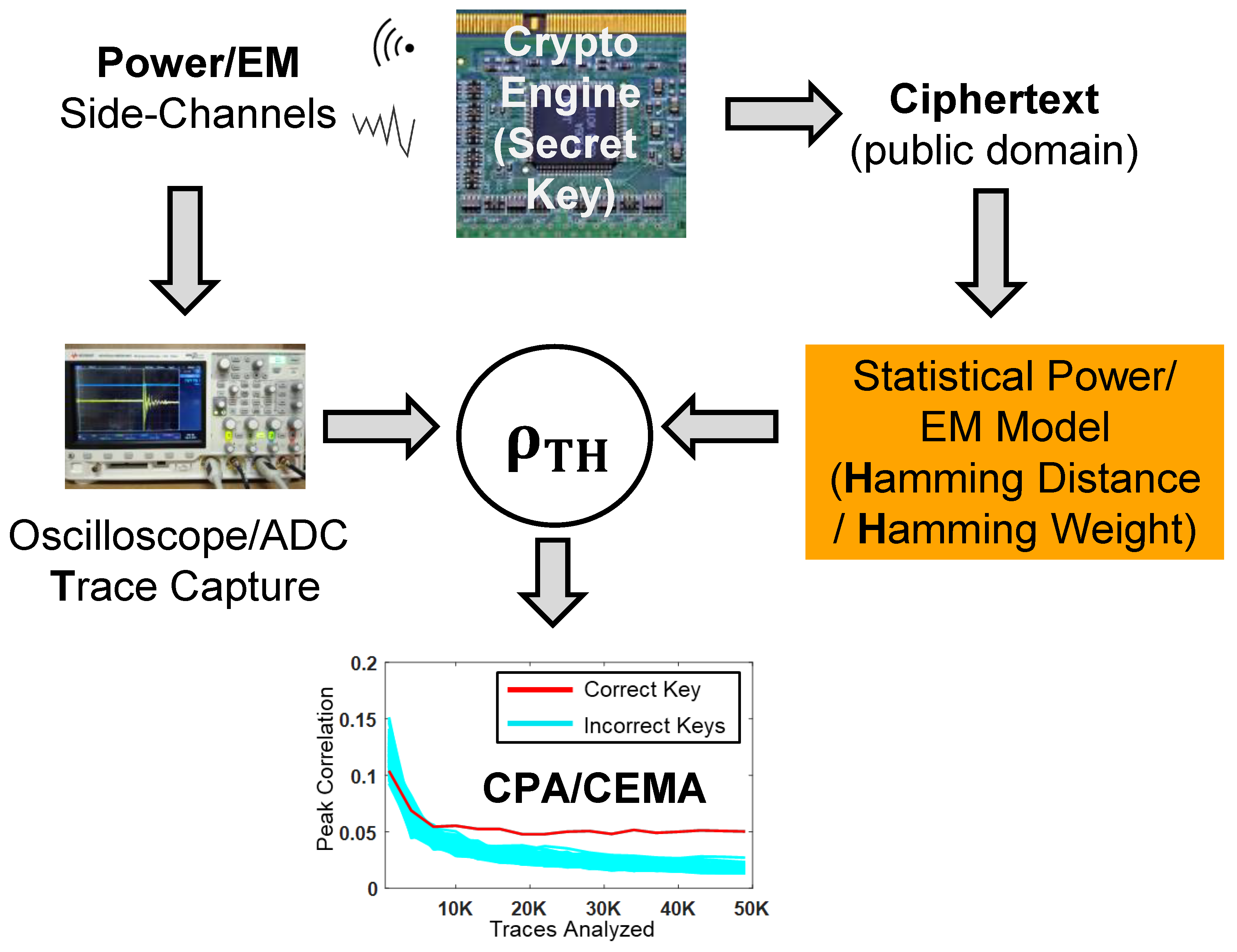
Cryptography | Free Full-Text | Electromagnetic and Power Side-Channel Analysis: Advanced Attacks and Low-Overhead Generic Countermeasures through White-Box Approach