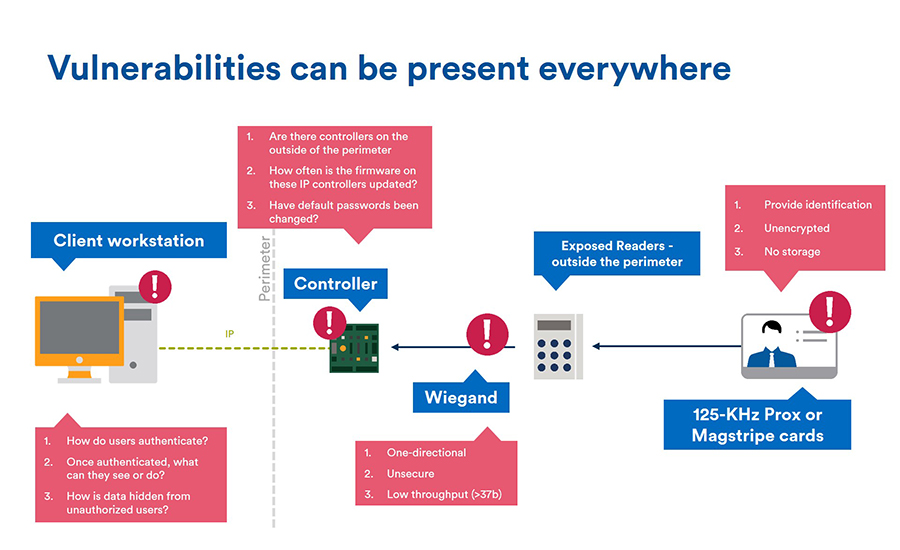
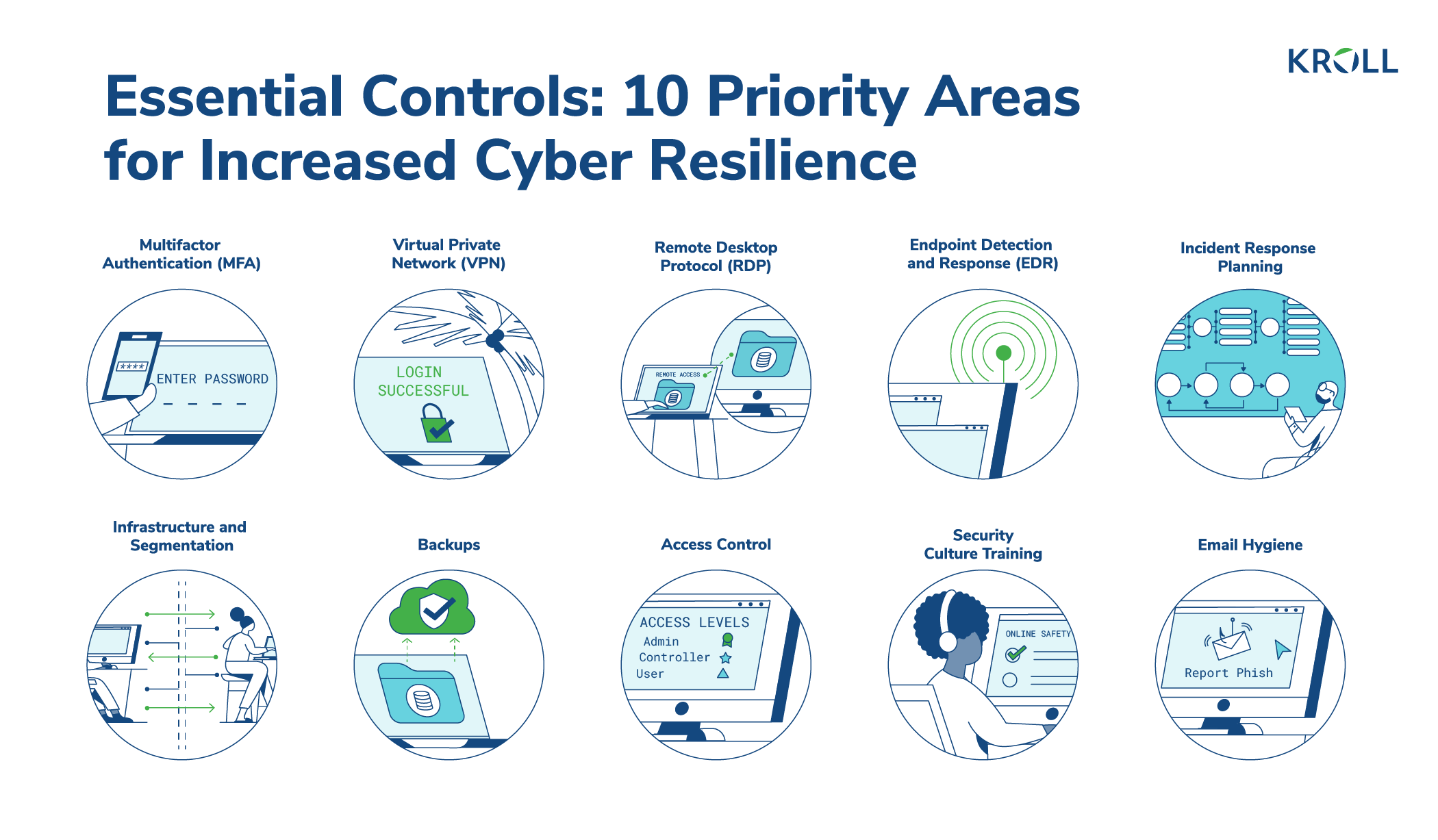
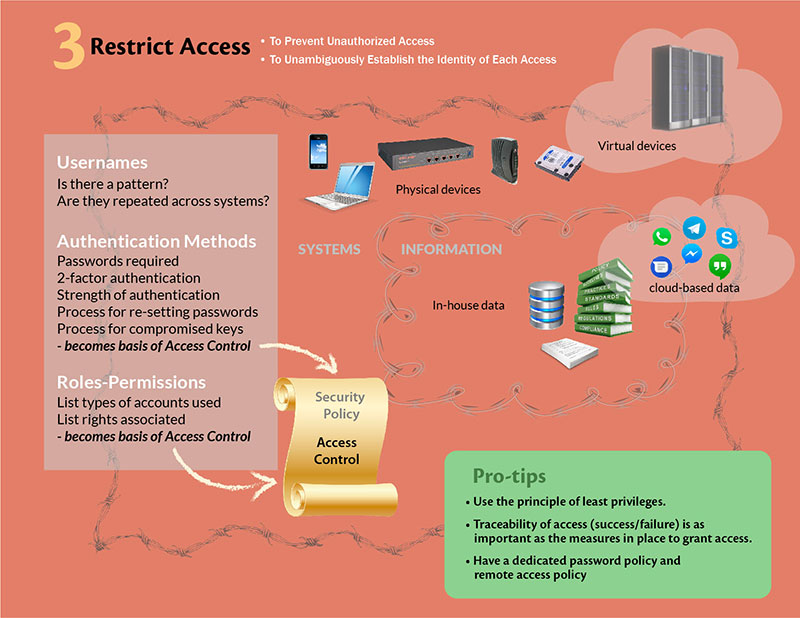
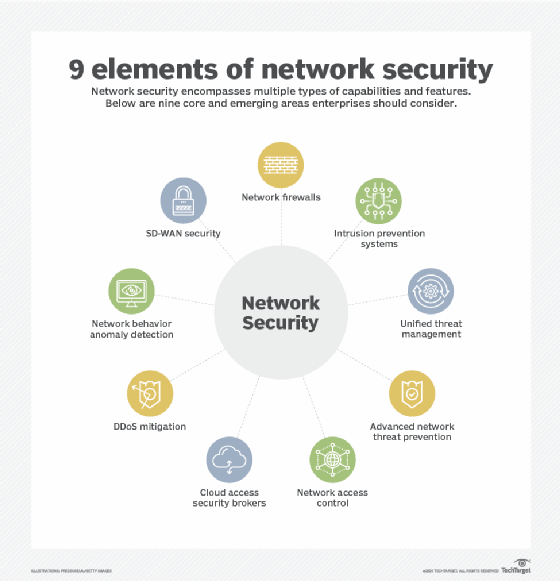
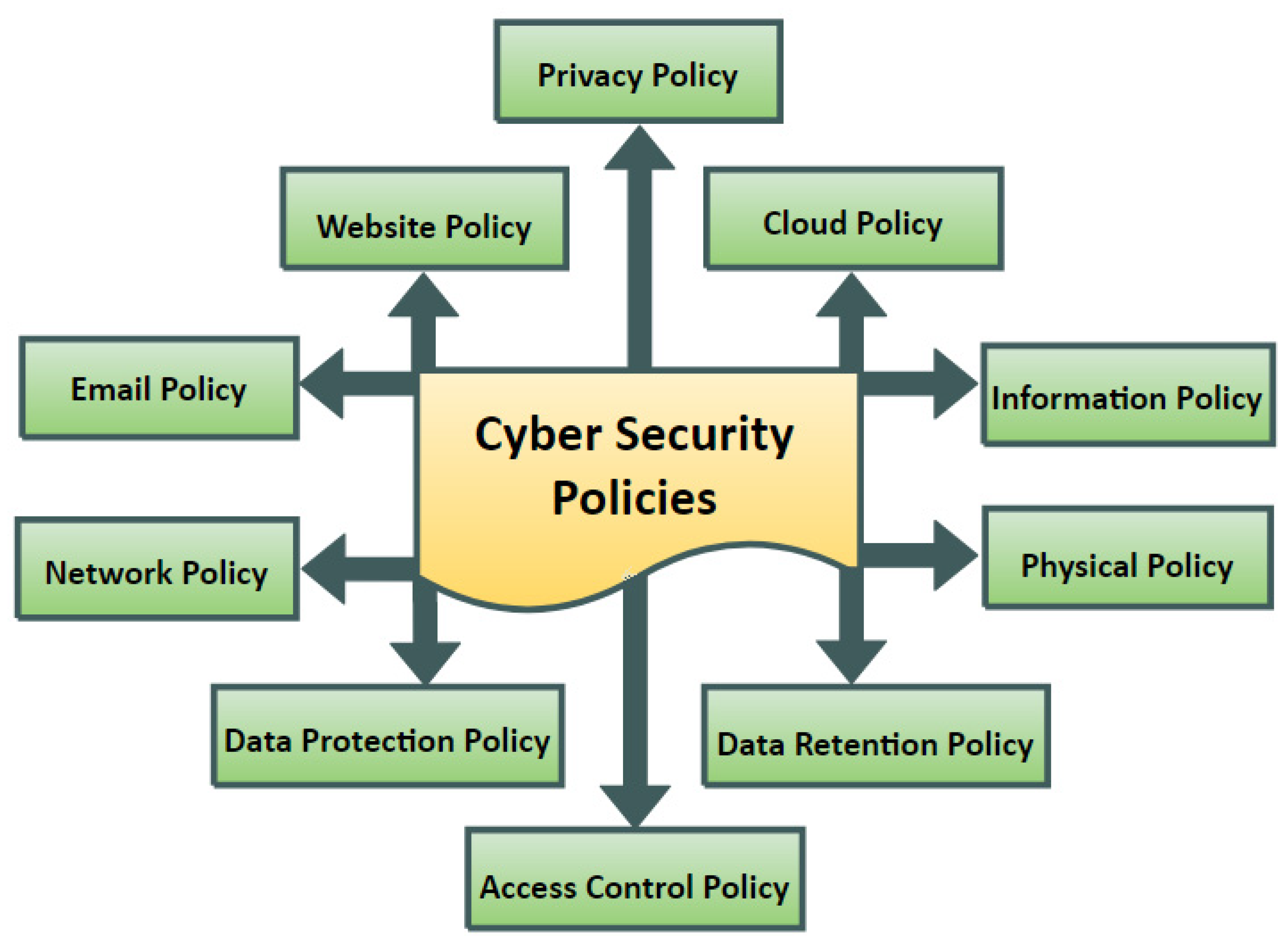
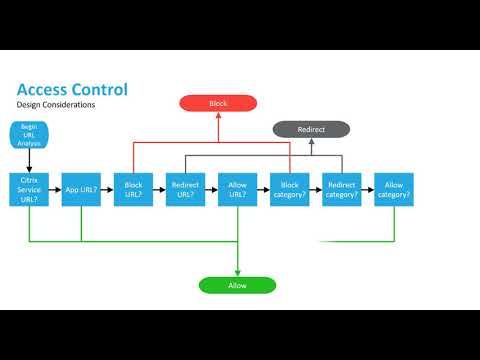
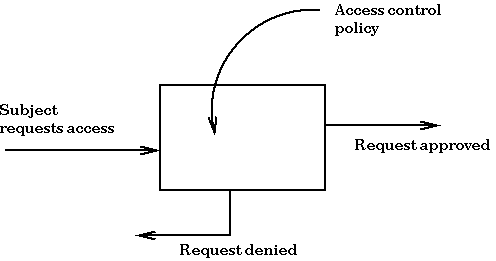
Access Control | User access control | Access Control system |Network access control | Infosec - YouTube

Free Online Course: Information Security - Authentication and Access Control from edX | Class Central

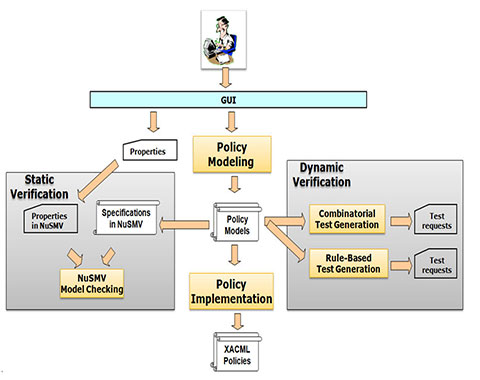
A systematic review on security in Process-Aware Information Systems – Constitution, challenges, and future directions - ScienceDirect