Network Security - Virus, Worms, Cookies, Spams, Trojan Horse, Firewall | Class 12 CS/IP | L8 - YouTube
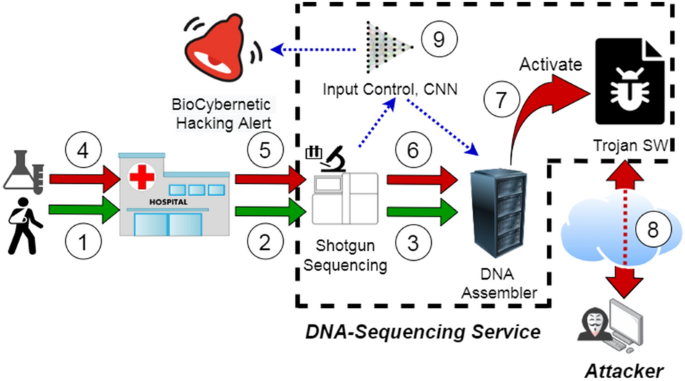
Using deep learning to detect digitally encoded DNA trigger for Trojan malware in Bio-Cyber attacks | Scientific Reports
Dynamic DNS Domain Name System No-IP Computer Icons, Remote Access Trojan, computer, mikrotik, multimedia png | PNGWing








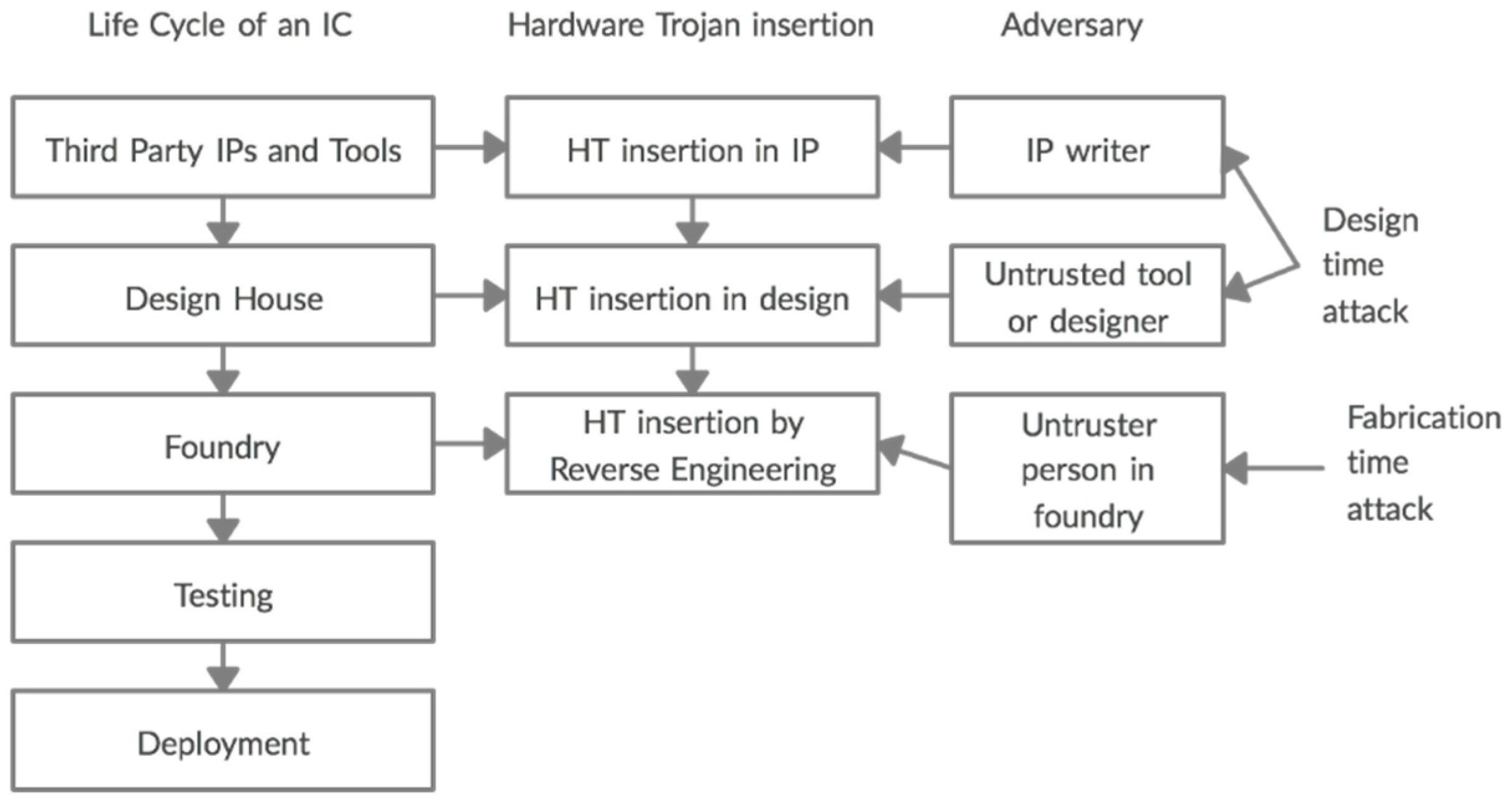


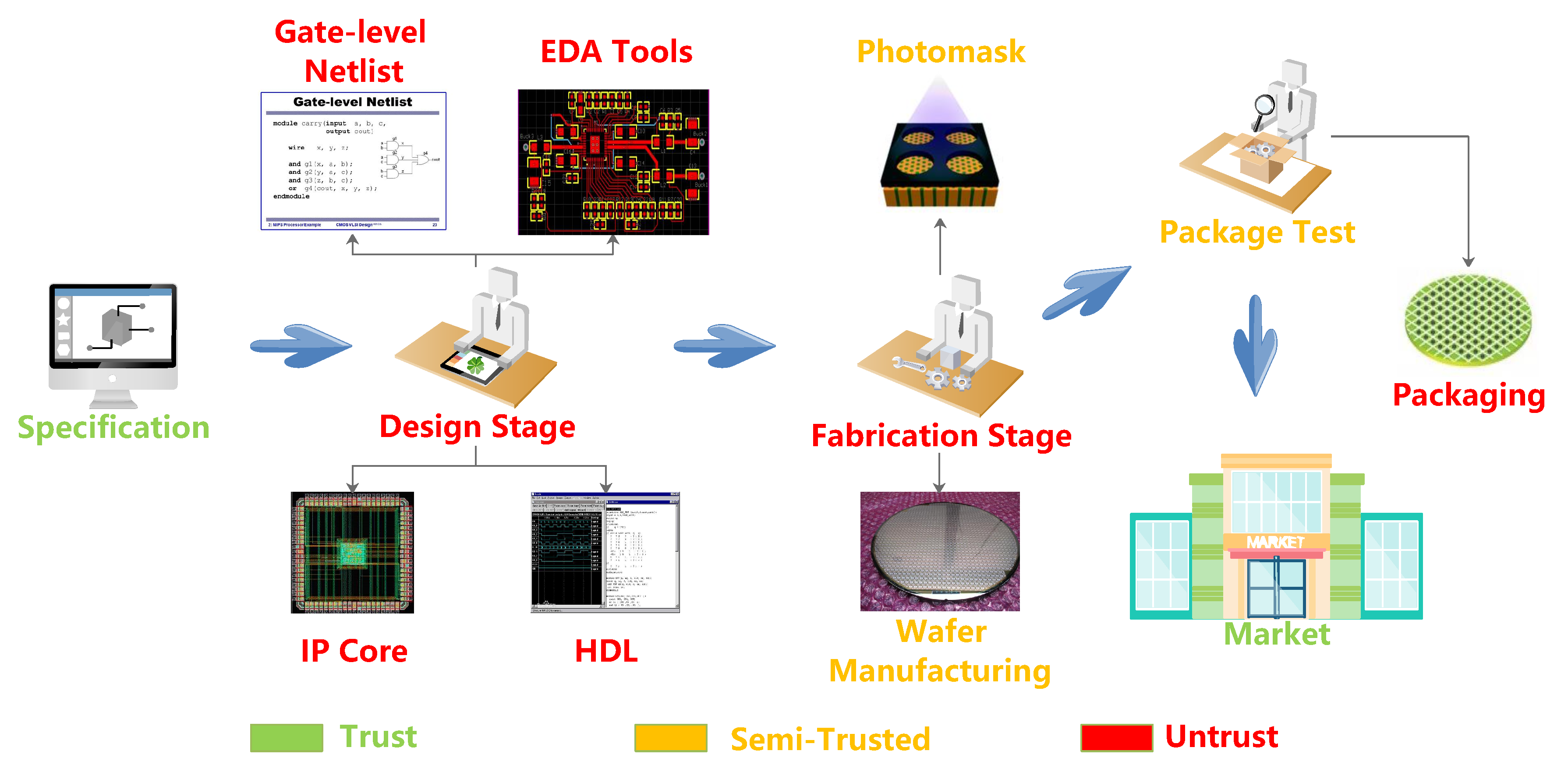
![PDF] Hardware IP Protection During Evaluation Using Embedded Sequential Trojan | Semantic Scholar PDF] Hardware IP Protection During Evaluation Using Embedded Sequential Trojan | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f07ba2d53b7870e8b1bb8f07a11d4b626a9624f3/4-Figure2-1.png)